Enigma (ENX) is a privacy-focused Web3 protocol built on an invisible and continuously adaptive cybersecurity architecture. Its core mission is to reverse traditional network security approaches, making infrastructure invisible rather than defended. ENIGMA integrates encrypted communication, stealth network routing, and decentralized identity into a unified ecosystem.
The ENX token sits at the center of this ecosystem, enabling network security reinforcement, resource allocation, governance, and access to privacy layers.

Project Concept
ENIGMA was created to address modern cyberattacks, most of which start with reconnaissance. Traditional systems constantly signal to attackers via open ports, DNS records, static IPs, and traffic metadata. Enigma defends digital self-sovereignty, giving users complete ownership over their data.
By removing “gatekeepers,” the platform ensures fair and open information flow, enabling full participation in the digital economy. Its infrastructure is censorship-resistant, protecting privacy while empowering users rather than exploiting them.
ENIGMA eliminates the attack surface entirely:
-
No discoverable infrastructure
-
No mappable networks
-
No metadata to analyze
The goal is not to detect attacks but to prevent them from starting.
Team & Founders
-
Marcus Crockett – CEO & Co-Founder: Experience in US Department of Defense, critical infrastructure, and financial security.
-
Harris Nussbaum – Co-Founder & Chief Architect: Creator of RAVID, 30 years in US Marine Corps signals intelligence.
-
Jennifer Raiford – CISO: Renowned cybersecurity and AI expert, known as “the Olivia Pope of Cybersecurity.
Core Principles
-
Stealth Networking – No open ports, DNS records, or routable endpoints; access is identity-based.
-
Moving Target Defense – Infrastructure components are ephemeral, identities rotate, network topology changes randomly.
-
Zero Metadata Architecture – Eliminates signals like traffic patterns, timing, or flow volume for analysis.
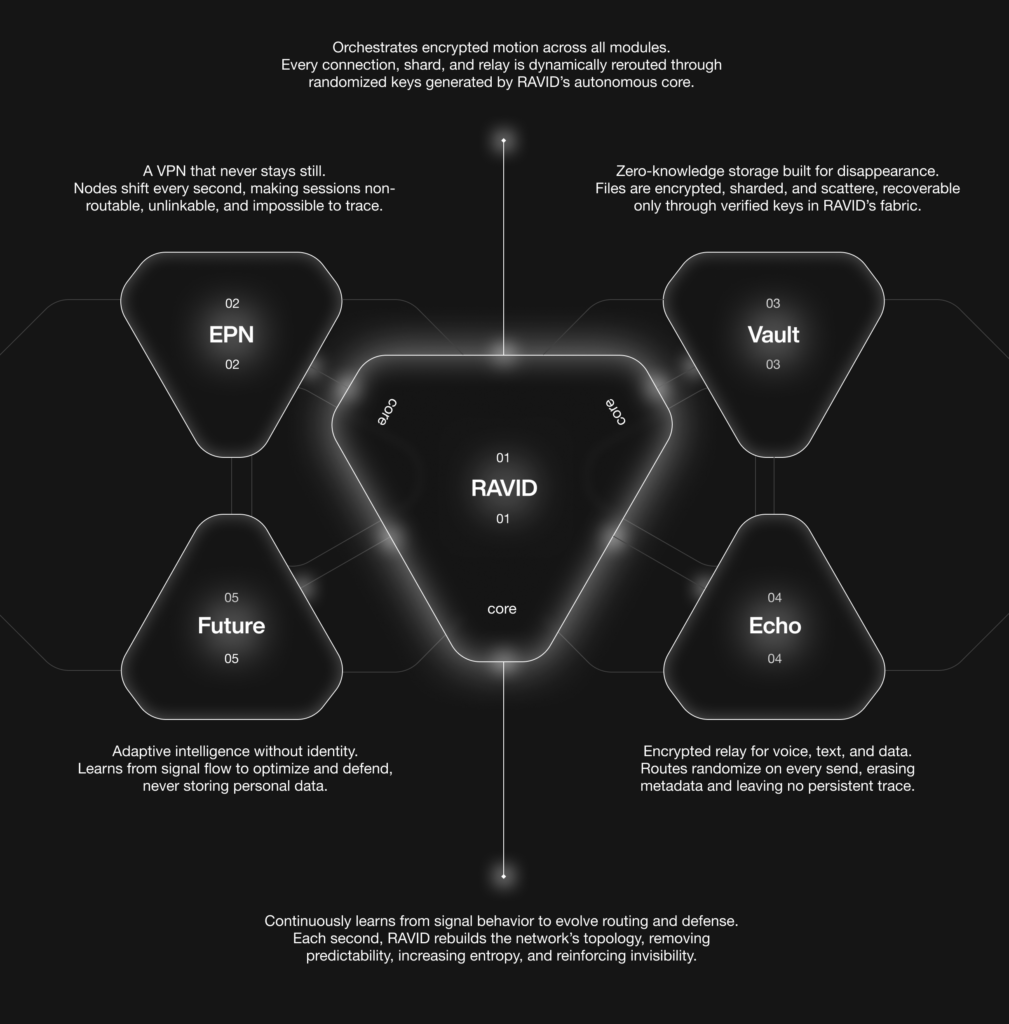
RAVID Framework
RAVID (Randomized Adaptive Virtual Infrastructure Defense) is Enigma’s technical backbone. It continuously transforms infrastructure to make it an unmappable and ephemeral target:
-
Service identities constantly rotate
-
Resources are temporary
-
Authorization points are dynamic
How It Works
Built on OpenZiti zero-trust architecture:
-
All connections use mutual TLS
-
Identity-native routing controls access
-
Resources instantiate only when authorized
-
Traffic flows through invisible channels and disappears after use
Components
-
RAVID (Core): Manages encrypted traffic between modules with dynamically generated keys and constantly rebuilt topology.
-
EPN (VPN): Rotating nodes provide untraceable VPN service.
-
Vault (Storage): Zero-knowledge encrypted, sharded, and distributed storage; accessible only via verified keys.
-
Echo (Communication): Encrypted messaging with random routing, removing metadata.
-
Future (Adaptive AI): Identity-free AI layer optimizes and defends the network.
Ecosystem
-
EPN (Enigma Private Network): Invisible, identity-controlled VPN replacement.
-
Echo Messenger: Secure messaging with quantum-resistant encryption and metadata protection over EPN.
-
Vault Wallet: Combines cold wallet security with hot wallet functionality without leaking keys or metadata.

ENX Token
ENX powers access and governance across Enigma products.
Token Details:
-
Name: ENX
-
Total Supply: 100,000,000 ENX
-
Max Supply: 100,000,000 ENX
-
Circulating Supply: 62,570,000 ENX
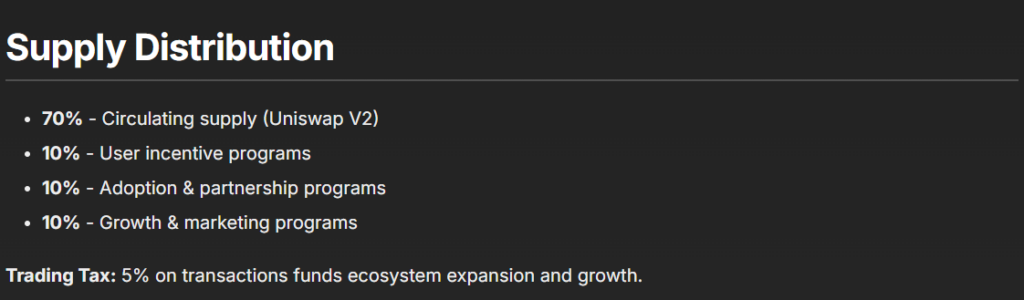
Distribution:
-
70% Circulating Supply (Uniswap V2)
-
10% User Incentives
-
10% Adoption & Partnerships
-
10% Growth & Marketing
Use Cases:
-
Tiered access to EPN, Echo, Vault
-
Staking to enhance network security
-
Participation in revenue distribution
-
DAO governance voting
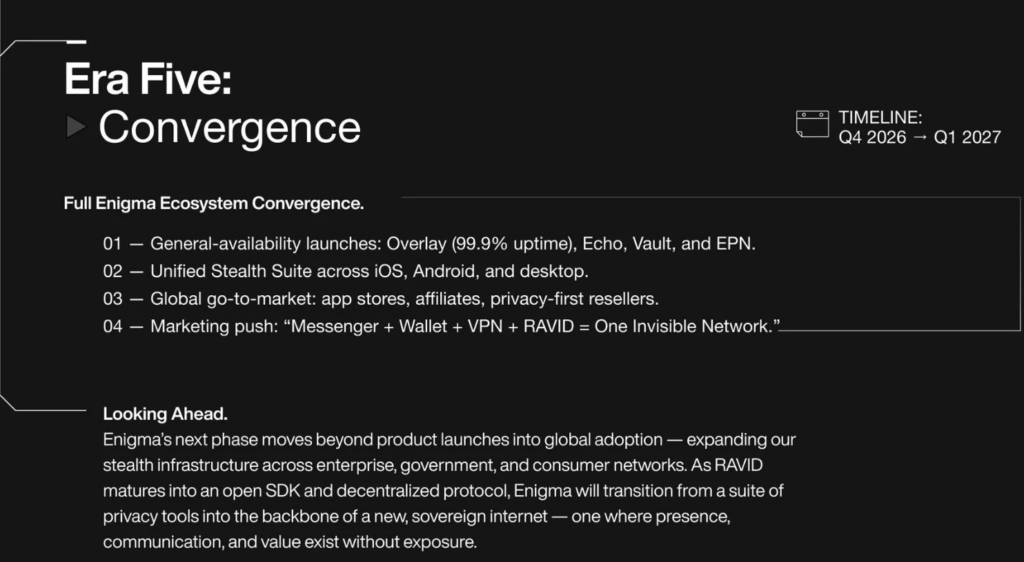
Roadmap – Era Five: Convergence
-
Product Launches: Overlay (99.9% uptime), Echo, Vault, EPN GA releases
-
Platform Coverage: iOS, Android, and desktop Stealth Suite package
-
Market Entry: Global distribution via app stores and privacy-first channels
-
Marketing: Unified messaging highlighting Messenger + Wallet + VPN + RAVID integration
Key Features
-
Fully invisible infrastructure
-
Zero metadata generation
-
Continuously adaptive target architecture
-
Quantum-resistant design
-
Web2 and Web3 integration
Official Links
You can freely share your thoughts and comments about the topic in the comment section. Additionally, please don’t forget to follow us on our Telegram, YouTube and Twitter channels for the latest news and updates instantly.


