Another security incident has been added to the growing list of blockchain hacks in recent years. GANA Payment, a crypto payment project, has fallen victim to a major attack carried out on the Binance Smart Chain (BSC). According to information confirmed by the project team, attackers exploited a critical vulnerability and stole more than $3.1 million. The attack did not remain confined to BSC; once the funds were moved to the Ethereum network, the incident evolved into a multi-chain and more complex operation.
Such hacks are known not only for their financial impact but also for the severe blow they deal to a project’s credibility and the broader ecosystem. The attack on GANA Payment is worth examining closely both in terms of how it was executed and how the attackers attempted to erase their tracks.
Fund Drain Begins on BSC
The hack began with unauthorized withdrawals from GANA Payment’s smart contracts on BSC. By exploiting a system vulnerability, the attacker quickly gained control of large amounts of assets.
The first portion of stolen funds consisted of 1,140 BNB, worth approximately $1.04 million at the time. The attacker immediately mixed these BNB tokens through Tornado Cash, a tool frequently used in hacks because it makes tracing funds nearly impossible. The attacker’s decision to exit the BNB Chain early is a classic — and highly effective tactic to disrupt forensic tracking.
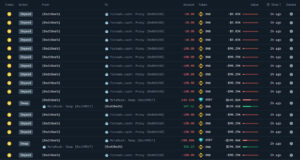
Cross-Chain Escape: Funds Moved to Ethereum
In the second phase, the attacker transferred the stolen funds from BSC to Ethereum via cross-chain bridges. Once on Ethereum, the funds were consolidated into 346.8 ETH, valued at around $1.05 million.
On Ethereum, the attacker once again used Tornado Cash to mix the funds — a widely used strategy for removing transaction traces and redistributing stolen assets.
At this point, the attacker’s goals became clear:
- spreading funds across multiple chains,
- complicating the transactional trail,
- making tracking significantly harder,
- breaking trace continuity between networks.
This method is extremely effective in large-scale thefts where attackers aim to cover their tracks.
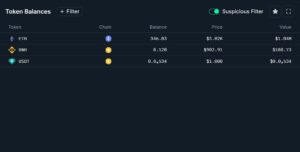
The Unmoved 346 ETH: Waiting or Planning?
One of the most intriguing details is that approximately 346 ETH (worth around $1.046 million) remains untouched. These funds are currently parked at:
0x7a503e3ab9433ebf13afb4f7f1793c25733b3cca
There are several possible explanations for why the attacker has not moved these funds yet:
- waiting for blockchain security firms to ease monitoring pressure,
- planning to split and move the funds slowly over the coming days,
- waiting for higher mixer liquidity or optimal timing,
- suspecting surveillance on certain wallets or bridges and avoiding risky moves.
This type of waiting strategy is common in major hacks. Attackers often freeze funds for weeks or even months to break tracking patterns.
Assessment: Multi-Chain Hacks Becoming More Dangerous
The GANA Payment incident once again highlights how critical and fragile blockchain security is today. Cross-chain bridges, in particular, are increasingly being used by attackers, making hacks more complex and significantly harder to trace.
When anonymity tools such as Tornado Cash come into play:
- on-chain analysis becomes far more difficult,
- fund origins become obscured,
- attacker behavior becomes unpredictable.
For multi-chain projects, the security risks are much higher than for single-chain architectures. The GANA Payment case is a strong reminder of how quickly projects with weak security frameworks can become targets. It serves as a major warning for developers, investors, and the entire crypto ecosystem: Security must be designed from the beginning — not fixed after a project launches.
You can also freely share your thoughts and comments about the topic in the comment section. Additionally, don’t forget to follow us on our Telegram, YouTube, and Twitter channels for the latest news and updates.


