The security of the decentralized physical infrastructure network (DePIN), Io.net, was recently violated by a cyberattack. Malicious users performed an SQL injection attack by exploiting the exposed user ID tokens. The outcome was the modification of device metadata in the GPU network was illegal.
The CISO of Io.net, Husky.io responded immediately by locking down the network with patches and improvements. Due to the powerful permission layers of their GPUs, the real hardware of the GPUs survived the attack.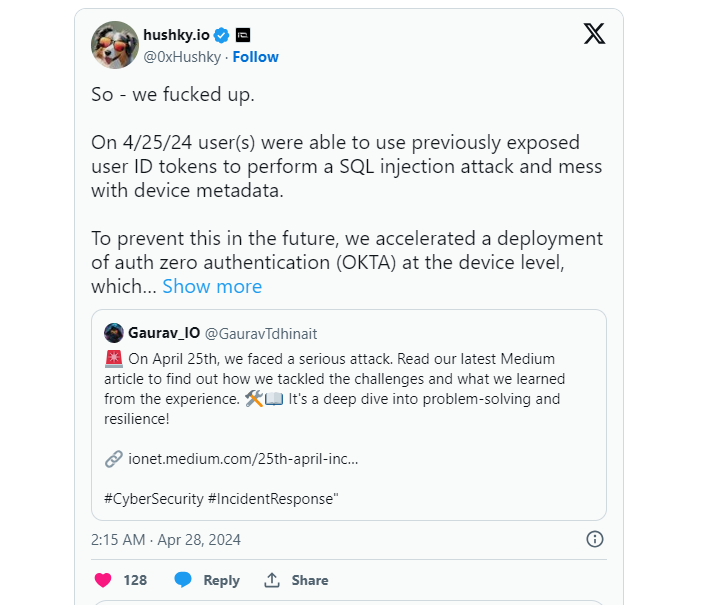
Between 07:27:43 and 07:29:05 AM PST on April 25, write operations increased within the GPU metadata API to trigger the breach detection and the alarm activation.
The security measures included making it more complex to inject SQL queries into the APIs and helping to document illegal attempts better. To complement the problems of universal authorization tokens, a user-specific authentication solution was promptly deployed using Auth0 with OKTA.
Furthermore, the anticipated reduction in supply force participants was aggravated by the fact that this security patch update happened at the time when one of the reward program snapshots occurred. As legitimate GPUs did not restart and update, they were unable to use the uptime API, resulting in a drastic drop in the number of active GPU connections from 600,000 to 10,000.
In response to these issues, we initiated Ignition Rewards Season 2 in May to stimulate the participation of the supply side. The supply chain collaboration regarding device upgrades, reboots, and reconnections is a continuous process.
Io.net API Vulnerability Exposed
The problem with the intruder was flaws in the proof-of-work (PoW) method used to detect fake GPUs. Attacking tactics intensified as a result of all aggressive security measures that were applied even before the incident, thus proving the need for continuous security research and advancement.
To present the content in input/output Explorer, the attackers exploited a vulnerability in an API. Therefore, in the process, user IDs were exposed upon device ID searches. Data had been dumped into the database by some malicious attackers a few weeks before the incident.
The attackers managed to get into the ‘worker-API,’ which allowed them to alter device metadata without needing user-level authentication by using a valid universal authentication token.
For early threat detection and neutralization, Husky.io emphasized continuous full assessment and penetration testing of public endpoints. Despite hurdles, we continue to rebuild network connectivity and stimulate supply-side participation in order for the platform to remain operational and deliver hundreds of thousands of compute hours per month.
Io.net wanted to integrate Apple silicon chip technology in March to enhance its AI and ML offerings.


